Phishing: How Hackers Exploit Human Nature
Phishing scams are everywhere, emails, texts, calls and even QR codes. Learn how hackers use psychological tricks to steal your data, how to spot red flags, and see a real phishing attack demo in action.

Phishing is one of the most common and effective cyber threats today, targeting both individuals and organisations. Phishing attacks are used to steal sensitive information, such as usernames, passwords, and even payment details, by impersonating legitimate sources. Alarmingly, phishing succeeds not because of technical flaws but because it exploits human psychology.
In this post, we’ll break down how phishing works, why it’s so dangerous, and walk through a real-world demo that shows just how simple these attacks can be.
What is Phishing?
Phishing is a type of social engineering attack in which attackers pretend to be legitimate, trusted entities like your bank, boss or even a delivery service, to trick people into handing over information or downloading malicious software.
Phishing attacks can occur through email, SMS (known as smishing), or over the telephone, (known as vishing). The core tactic behind phishing is deception, attacks will mimic familiar and trusted organisations to manipulate victims.
Phishing is generally the term used when the attack is targeted at masses of people. Attacks can be more targeted and personalised, such as spear-phishing, which is targeted at certain groups of people or a department within an organisation. Similarly, a whaling attack is a spear-phishing attack that is exclusively aimed at a high-level executives, such as senior leadership team members and CEOs. The goal is always the same: manipulate human behaviour for access.
How to spot a phishing email?
Modern phishing attacks are getting harder and harder to spot. Emails often appear identical to the legitimate version, and phishing websites can be near replicas of the genuine site. However, there are several things to watch out for.
- Urgency and Pressure: Phishing attacks always want you take some form of action, whether it be filling out a form, clicking a link, or downloading something. They usually employ urgency in to this too, where they want you take action now.
- Spelling and grammar mistakes: Phishing emails also generally contain subtle spelling or grammar mistakes. Check the body of the text, the name of the company, the email domain, the subject, even the footer of the email! These mistakes may be subtle, such as ‘0’ in place of ‘o’.
- Attachments and/or Links: Always hover over the attachment or link, so you can see the actual URL destination. In any event, you should always make your own way to a website, rather than clicking a link inside an email.
Remember – phishing attacks always want you to do something, to take some sort of action or provide something.
A phishing demo – How it works
To demonstrate how easily phishing attacks can be orchestrated, I created a phishing page that mimics a Microsoft login page. Initially, the user receives an email inviting them to view a file that has been shared with them by a colleague Jemma Johnson.
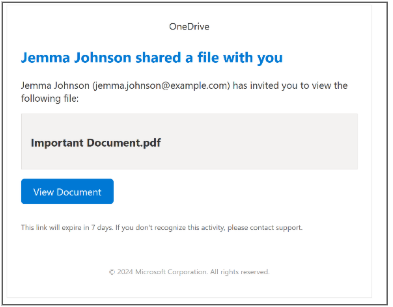
The user clicks the blue button to view the document. They are then taken to a Microsoft login page. This is a fake login page that I created, it mimics Microsoft’s sign-in page, although there are a few discrepancies.
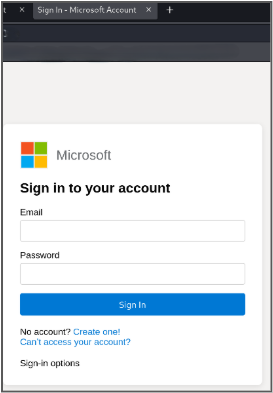
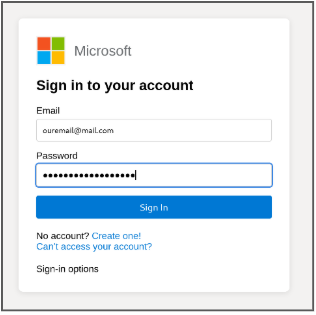
The user enters their email and password. They do not suspect anything because it is not uncommon to have to log in to an account to view and access shared files or documents.
After the user has entered their email and password, they seem to be redirected back to the Microsoft login page again. This tactic is commonly used in phshing attacks to avoid suspicion. The user may suspect they just entered the details incorrectly
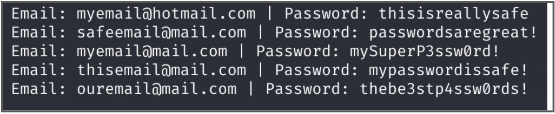
Unbeknownst to the user, a backend script is capturing the credentials and storing them on an attacker-controlled server. The attackers now has the victim’s Microsoft credentials.
It looks simple doesn't it. Did you spot the differences between the fake Microsoft login page and the real one?
Some Real World Examples
I’ve received plenty of convincing phishing messages myself. There is one I remember during the COVID-19 pandemic pretending to be from the NHS offering me the vaccine and asking for my personal details.
Just recently, I got a smishing text claiming to be from my local pharmacy, asking me to book a flu jab through a Google Calendar link sent from a random mobile number.
There’s a common WhatsApp scam doing the rounds recently, where a “daughter” claims to have lost her phone and urgently needs money from her mum.
Another common one that springs to mind, phishing emails informing me my parcel is waiting to be delivered to me, or that I missed the delivery and I need to rebook it.
Phishing works because its plays on psychology not technology. The attacks are cheap, easy and highly successful. The more we understand how they operate, the better equipped we are to spot the signs before it’s too late.
Stay sceptical. Stay sharp. Stay safe!